Marketing Cloud Security part 3: Data visibility
In the final post of our series on securing your data on Salesforce Marketing Cloud, we will explore the options available to control data visibility. This is particularly important when dealing with personally identifiable information (PII) or protected health information (PHI). By implementing these options, you can ensure that sensitive data remains protected and only visible to authorized users.
This is the third and last post in the series. The first post here is about securing access to the marketing cloud. The second post here is about securing data in the platform.
There are three options for controlling Data Visibility:
- Tokenized sending
- Field-level encryption
- Transparent data encryption
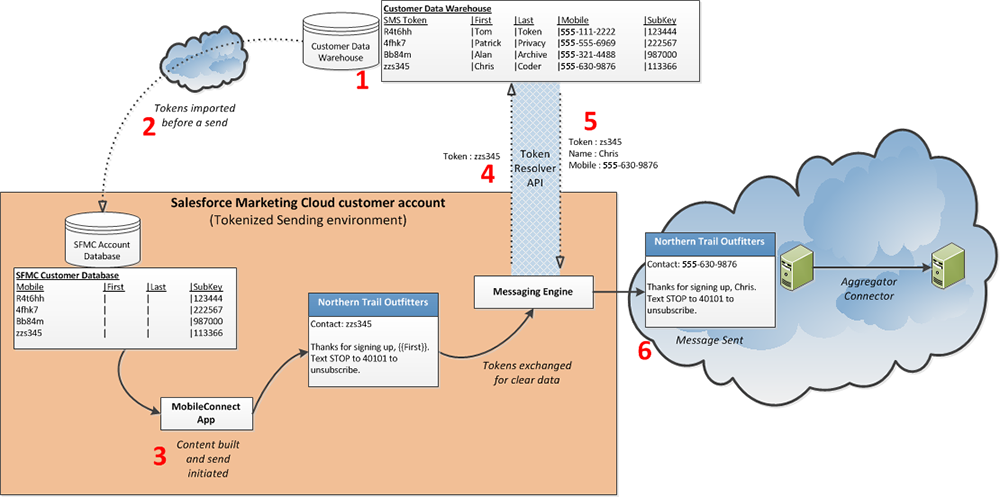
Tokenized Sending:
Tokenized sending involves using unrecognizable text values (tokens) for attributes instead of actual send attributes. The tokens are stored in the Marketing Cloud, and during sending, they are resolved by making a call to a detokenization server. This ensures that the actual values are not stored in the Marketing Cloud and are only used for that specific send.
The below picture depicting a tokenized sending is from Salesforce help documentation. You can refer to the same here.
Field Level Encryption (FLE)
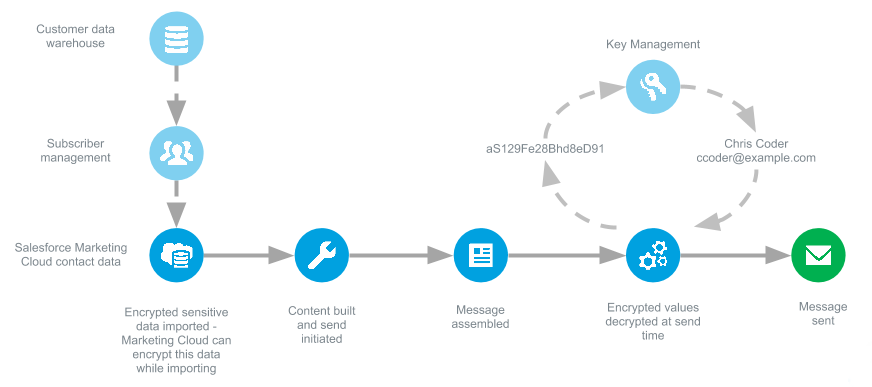
FLE allows you to encrypt data at rest, which is then decrypted at the time of sending. There are two ways to implement FLE:
- Encrypted in, encrypted out: You encrypt the data on your own and import it into the Marketing Cloud. Any exported or retrieved data remains encrypted.
- Clear in, clear out: Salesforce encrypts sensitive data upon import. Any exported data will be decrypted. Key management is used to store necessary keys for encryption and decryption.
The below image from salesforce help documentation depicts a send in an encrypted environment. Complete details can be found here.
Transparent data encryption
Transparent data encryption focuses on encrypting the underlying database or file system. This ensures that the data is protected and compliant with encryption requirements for compliance or legal needs. Users with proper access will be able to view the data without any changes to the application.

















No comments:
Post a Comment